|
|
TimeLG - Mobster Chaser - The prohibition car racer - Orchids Guide! - Forum for Blood Brothers - موسوعة الحلويات الباردة 2014 - 햇살론 생계자금, 대환자금 자격조건 승인률 높은곳 상담 -
 | AIM Buddy Icon Stealer is a brand new program for AOL Instant Messenger (AIM) that allows you to Steal Buddy Icons from all your AIM buddies. That means you can have and use any of the icons they have used! With Buddy Icon Stealer you can: - View and save all Buddy Icons used in AIM - Steal and use ...
|
SiteThief (in Download Managers)
 | Site-Thief is a website downloading software tool. It gives you the ability to download select portions or the entire content of a website and store it on your local hard drive for off-line use. Features: • Easy to use • Unattended operation • System notifies you when free updates are availabl...
|
SiteThief (in Download Managers)
 | Site-Thief is a website downloading software tool. It gives you the ability to download select portions or the entire content of a website and store it on your local hard drive for off-line use. Features: • Easy to use • Unattended operation • System notifies you when free updates are availabl...
|
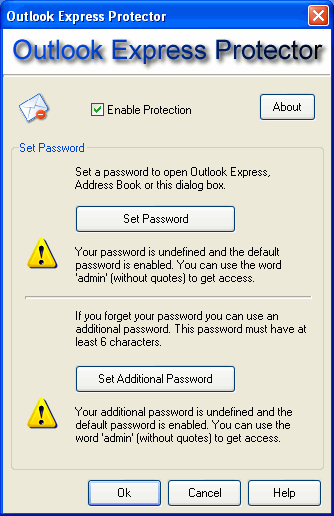 | Outlook Express Protector is designed for controlling access to Outlook Express and its e-mail and address data bases. It does not encrypt protected files and folders, however no programs can get access to them when the program is active. When you try to start Outlook Express or open Address Book, t...
|
 | Outlook Express Protector is designed for controlling access to Outlook Express and its e-mail and address data bases. It does not encrypt protected files and folders, however no programs can get access to them when the program is active. When you try to start Outlook Express or open Address Book, t...
|
Zapeze (in Security)
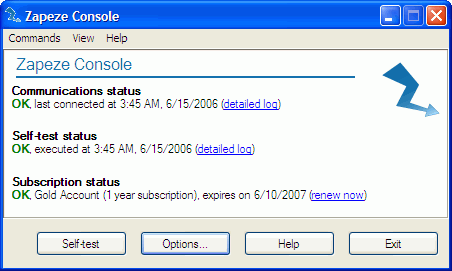 | Zapeze prevents identity theft and protects your sensitive data allowing you to erase your hard disk remotely, if your laptop or desktop computer has been stolen. You manage your computers registered to this service via our secure web interface. If one of your computers is stolen, you simply log on ...
|
 | Learn how to Spy Proof your computer in 4 easy steps! Inside SPY PROOFING MY COMPUTER you will learn: Do I need to Spy Proof my Computer? Scams Types Of Computer Recording Devices Hardware Keyloggers Removal Of Hardware Keyloggers Surveillance Spy Software Vs Adware What Is Surveillance Spy Software...
Tags: spy, proofing, spyware, adware, keylogger, remove, detect, destroy, popups, scam, identity, theft, steal, |
|
|






