|
|
Order by Related
- New Release
- Rate
Results in Title For breach of trust
 | T2U is a software deployment, patch management and license tracking system. T2U dramatically decreases number of software products included into the main packages. Since designing large packages is costly it always saves a good deal of money. .. |
|
 | Trust Backup is a solid backup solution you can trust you most valuable data to. The program functions fully automatically and supports all storage media, including hard-drive, floppies, CDs, external drives, remote servers (via FTP) and even e-mail. Log, scheduler, profiles and compression options are available, so you can monitor the process of backup and conserve disk space as well as perform different types of backup fully automatically. ..
|
|
 | Attach a digital signature, which is legally binding and equal to a handwritten signature, to a document. Create the document within PC-TRUST Document Signer or Microsoft Word, or WordPad. E-mail the document from within the editor instead of faxing or mailing a document with a handwritten .. |
|
Results in Description For breach of trust
 | Xeon Personal Firewall is one of the easiest firewalls to setup and use. Xeon will ask which programs should have access to your internet resources and will detect and prevent any possible breach of your computer security. You have full control of your internet resources with Xeon Personall Firewall... |
|
 | Can you really trust content stored by online service providers? Since BarracudaDrive is exclusively hosted by you, it becomes your personal cloud, allowing you to store and access your files and appliances anytime from anywhere...
|
|
 | The most simple way for the potential intruders is to write something into startup section of the registry. A number of trojans work this way. This can be done via network, without being physically present at the attacked computer! Having tested our Windows network we discovered that a half of all workstations had their registry open for everyone! The system registry has some vital keys which, if tampered with, make a security breach, destroy data. You can easily monitor the registry on the local or remote computer with our AxTNTRegSecurity control. It is another descendant of the common ancestor of all components which deal with different aspects of Windows NT .. |
|
 | Yapp the project planner, Keep track of what to do and who's doing it. Rule based planning allows you to get some real help not only a controlled drawing environment. Most other project planning tools are ok drawing environments but they fail in coordinating available resources and their use. They do not give you any or only modest support in rule based planning. This project planning tool gives you up to date warnings on common rule violations like resource overuse, deadline breach, and dependency violations, information that is crucial to you in order to build a realistic and working project plan...
|
|
 | Anti-spam software for Windows. It accepts emails from senders you trust while asking unknown senders to verify themselves by replying to an email. After positive verification it adds them to your approved sender list and delivers all their messages... |
|
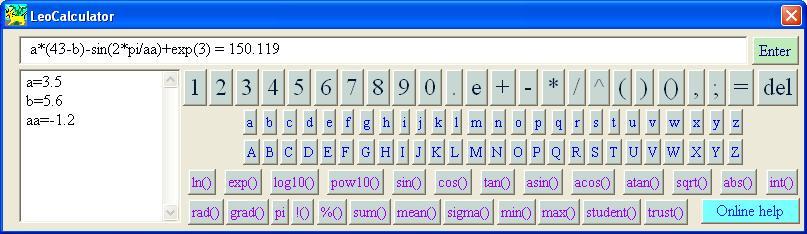 | LeoCalculator is an application for performing calculation of mathematical expressions that could include not only basic operations but also functions and brackets.
Edit box "Expression" has to contain a string of mathematical expression that is supposed to be calculated.
It can contain:
numbers in with or without decimal point and with or without a power of 10 like 1.2e-2 or 3.E3;
pi in this application is equal to 3.141592653;
basic mathematical operations +,-,*,/;
power of grade operation ^ used like 2^3 = 8;
brackets determining order of operation execution;
elementary mathematical functions: sin,cos,tan,asin,acos,atan,ln,log10,exp,pow10,abs,sqrt; basic statistical functions as sum, mean, sigma (standard deviation) student and trust for calculation probability and trust interval. Arguments of the functions have to be an expression surrounded brackets;
Variables can be declared and edited separately from formula and
can be any combinations of letters and numbers without spaces and reserved words: value expressions as usual are numbers but in most cases it could be mathematical expressions too...
|
|
 | Protect your personal messages with encryption keys of your choice. Tthen give the keys to people you trust. - When or if the need arises, change the keys to ensure continued privacy. Outstanding 'Identity Theft' software protection... |
|
 | Rental property management software / Trust Accounting Software was designed for use by the rental industry to suit residential and holiday unit management. Caretaker is one of the only products on the market today with NO ONGOING FEES.. |
|
 | Maximize your online product sales and increase your customer trust on your ecommerce business via our real time text based chat software. Best chatting software provides one to one or multi text chat with friends and family... |
|
 | ASP PHP based live customer support web chat script source code helps webmaster clients site visitors provides business solutions software set up online meeting interaction secure conversation improve clients satisfaction productivity trust.. |
|
Results in Tags For breach of trust
 | Rental property management software / Trust Accounting Software was designed for use by the rental industry to suit residential and holiday unit management. Caretaker is one of the only products on the market today with NO ONGOING FEES.. |
|
 | Arovax Shield software is dedicated to protect the home user's privacy. It Detects and Notifies you about all the Major online threats tried to penetrate your System, Isolates & Removes them. Arovax Shield protects your PC with bulletproof security from both known and unknown threats before they even get on your Personal Computer. Not a tech wiz? No problem - an easy-to-use interface and pre-loaded settings take the guesswork out of security. Don't hesitate. Download Arovax Shield now. Its completely free...
|
|
 | Shutdown mutiple remote workstations over a network with a number of options including aborting a pending shutdown. Supports both GUI and command-line interfaces. Groups of workstations can be saved in the GUI for later use in either interface... |
|
 | ..
|
|
 | Trust Backup is a solid backup solution you can trust you most valuable data to. The program functions fully automatically and supports all storage media, including hard-drive, floppies, CDs, external drives, remote servers (via FTP) and even e-mail. Log, scheduler, profiles and compression options are available, so you can monitor the process of backup and conserve disk space as well as perform different types of backup fully automatically... |
|
Related search : rovax shield,line interfacecommand lineremote shutdown,command line interfacechild watchdogexploit child,exploit child watchdog,backup trust backupOrder by Related
- New Release
- Rate
2010 security breach -
define security breach -
security breach database -
computer security breach -
facebook security breach -
|
|











