|
|
Order by Related
- New Release
- Rate
Results in Title For data hiding
 | Stego product for Windows with a CHAOS interface and a very large hiding capacity (~100% of carrier file). .. |
|
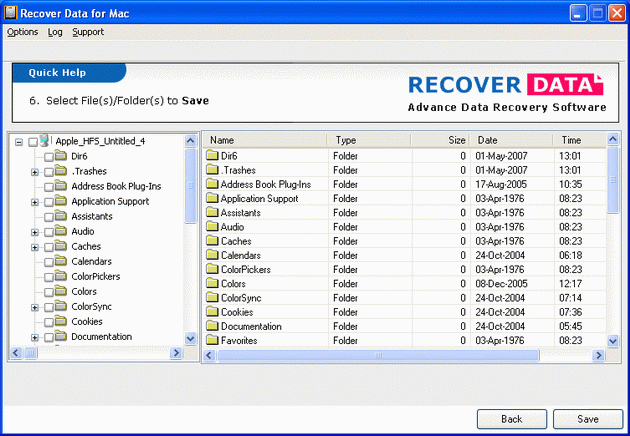 | Mac Data Recovery Software Tools to restore mac data from formatted, deleted, damaged HFS and HFS+ Mac Volumes. Software restore mac data, files and folders from apple Mac OS X Operating System which gets corrupted due to bad sectors, partition table corruption, disk initialization, master directory block or volume header corruption, catalog file corruption and catalog files node corruptions.
Recover Data for Mac Data Recovery Software is equipped with advance algorithm which performs exhaustive scan of the damaged drive and searches for the deleted, lost partitions, files and folders. Lost macintosh data from the deleted, formatted, damaged or corrupt mac volumes is effectively recovered by the Recover Data for Mac software. The recovered data is displayed in a tree like structure through which user can easily select the appropriate file and save to a working volume or disk. Software is a quick solution to restore mac volume data for successful Mac OS X recovery. Software supports recovery from HFS, HFS+ partitions of mac. Supports data recovery from Apple Mac OS X operating system as well as Apple Mac OS 9.x and higher. ..
|
|
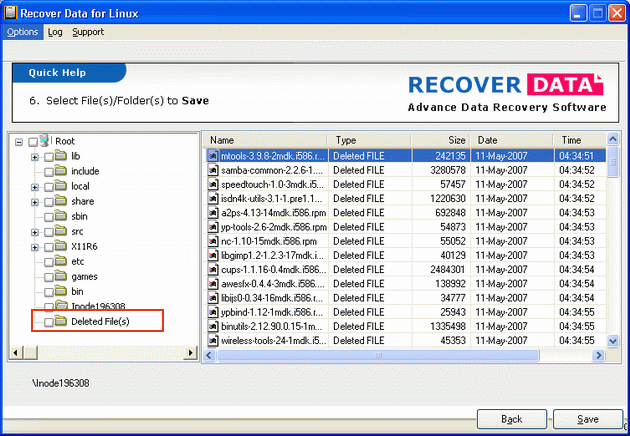 | Recover Data Linux Data Recovery Software, recovers and restores Linux data and files from the crashed Linux EXT2 and EXT3 partitions. Advance Linux Data Recovery Software restores Linux data, files and folders which gets corrupted due to viral infection, sudden system shut down, partition table deletion or corruption, operating system corruption, group descriptor block corruption or inode table corruption. Recover Data Linux Data Recovery Software uses advance algorithms & techniques to rescue data from damaged Linux partitions (Ext2 and Ext3). Get everything back using Recover Data Linux Data Recovery Software even when the Drive's Partition Table, Boot Record, Master File Table, or Root Directory is lost or corrupt. Linux Data Recovery Software recovers lost, deleted and formatted partitions or logical EXT2 and EXT3 partitions. Damaged or corrupted Linux data is effectively recovered by the Recover Data Linux data recovery software from the deleted, formatted, damaged or corrupt Linux EXT2 and EXT3 partitions. Software allows Linux file recovery from damaged Linux data volumes. Software recovers corrupt Linux partition and allows access to Linux files and data easily. Software offers quick solution to restore Linux partition for successful Linux data recovery. Software supports recovery from lost, deleted and formatted partitions or logical EXT2 and EXT3 Partitions. Features of Recover Data Linux Data Recovery Software - recover lost, deleted and formatted partitions or logical EXT2 and EXT3 Partitions; partial LVM Recovery; recover deleted Linux files; recover Linux EXT2 and EXT3 volumes with damaged Super Block or Inode List. Recover Data for Linux is best Linux partition recovery tool to get back deleted files & folders from formatted or deleted Linux EXT2 and EXT3 partitions. .. |
|
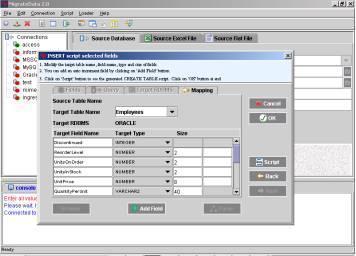 | Migrate-Data is a pure java and an extremely powerful enterprise data migration tool. It supports open source and commercial databases.
With Migrate-Data the user can easily extract, transform, load and integrate data from any-to-any databases. In addition the user can also perform customized data extraction from source and create customized target objects.
FEATURES
1.Migrates data to target database having same or different schema from the source database
2.Generates ..
|
|
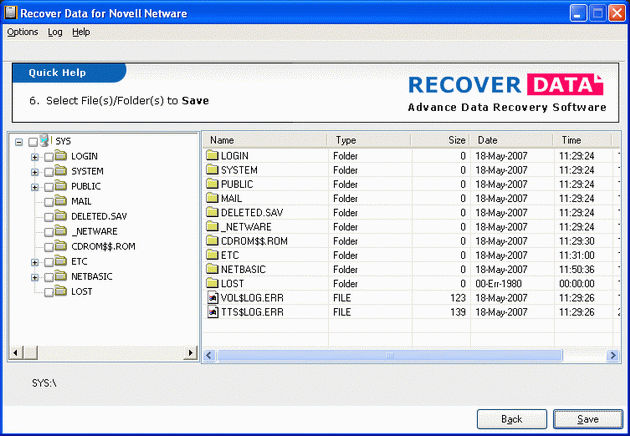 | Recover Data Novell Data Recovery Software is best Novell file recovery tool to salvages Netware data and files from the crashed Novell Netware (NWFS, NET386) volumes. Novell File recovery Software restores Netware data, files and folders which gets corrupted due to partition table deletion or corruption, operating system corruption, volume table and HotFix table damage, DET or FAT corruption, Pool table and leaf branch corruptions, and if VRepair fails to repair the corrupt volumes. Recover Data Novell Data Recovery Software uses advance techniques to salvage data from damaged Novell hard drive and searches for the deleted, lost volumes, files and folders. Damaged Netware volume data is effectively recovered by the Recover Data Novell data recovery software from the deleted, formatted, damaged or corrupt Novell NetWare volumes. Software allows Netware file recovery from sub allocated Novell data volumes and from the compressed files and directories has also become manageable. Novell Data Recovery Software recovers corrupt Novell Netware volume and allows access to Novell files and data even when the Novell volume(s) cannot be mounted. After complete disk scanning recovered files and Novell data is displayed in a explorer like structure through which user can easily traverse and select the appropriate files and save it to a working volume or disk. Software offers quick solution to salvage Netware volume data for successful Novell data recovery. Use Professional Novell Data Recovery Software at Recover Data to get back Novell data, files and folders which gets corrupted or damaged due to any reasons. Software supports recovery from NWFS, Net386 traditional partitions of Novell Netware. Supports data recovery from Novell 3.x to Novell 6.x. .. |
|
 | The router monitor is a utility to help you monitor the activity on your ZyXEL Prestige 100, 128, 202 or NETGEAR RT328, RH348 or D-Link DI-106 ISDN router. It works with router firmware version 1.50 to 2.50. The router monitor inserts an icon in the system tray. The icon shows if line 1 or line 2 are on-hook and if there is any traffic. The Router Monitor contains a TELNET emulator that enables you to do specialized router functions and configuration. Syslog messages from your router is also received by the router monitor. To help those who have problems with unwanted ISDN dialup by the Prestige router, a lan packet analyzer is included in the router monitor. The analyzer shows the information about the last lan packed that made the prestige dial the internet. You can also paste your own packets into the analyzer and have that analyzed. The router monitor can show statistics about past incoming and outgoing calls and show you graphs of the line utilization. To sumarize it all: A must have utility for your ISDN ..
|
|
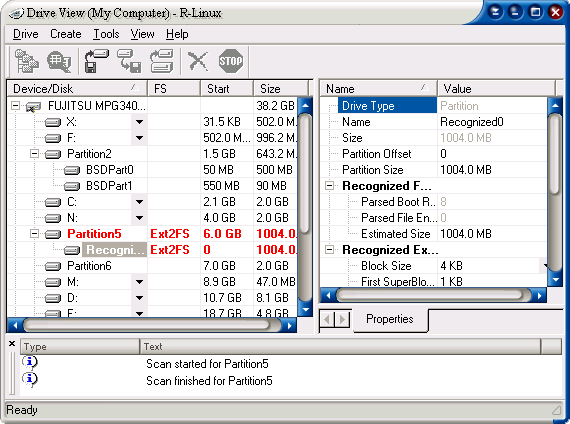 | R-Linux is a data recovery and undelete utility for Ext2FS (Linux) file system. File recovery after power failure, system crash, virus infection or partition reformation, even for the different file system. Unformat and unerase tool. Creation of image files an entire disk, partition or its part. Such drive image can be processed like regular drive. Recognition and parsing of Dynamic (Windows 2000/XP), Basic and BSD (UNIX) partitions layout schema. Localized names support.Recovered files can be saved on any (including network) disks accessible by the host operating system. .. |
|
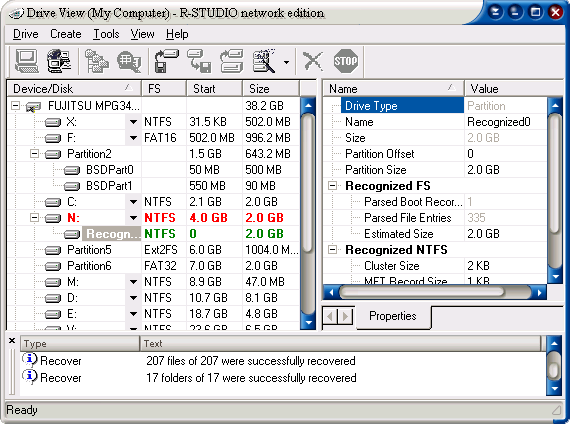 | R-Studio - the most comprehensive data recovery software and undelete tool supports FAT12/16/32, NTFS, NTFS5 (created or updated by Win2000), Ext2FS (Linux) file systems and recovers files both on local logical and physical disks and disks on remote computers over the networks, even if their partition structures are damaged or deleted. Unformat, unerase and file recovery after FDISK, MBR destruction, FAT damaged, virus infection. Creates drive image for further data recovery. Dynamic disk support. Damaged RAID (Volume and Stripe sets) reconstruction. Recovering encrypted files, compressed files and alternative data streams. File or disk content can be viewed and edited in the hexadecimal editor, which supports NTFS file attribute editing. R-Studio was created thanks to new unique technologies. Flexible parameter settings give you absolute control over data recovering. .. |
|
 | DataRestore can easily recover your deleted files, important data and lost partitions from all types of hard-disks, on all major Windows operating systems! You can now recover deleted data on your hard-drive, even if the partition table is lost! .. |
|
 | Automotive and powersports data that includes all features, options, warranties, specifications, general details, available colors, dimensions, weights, angles, capacities for all vehicles from 1981 to present year. The library also includes media. .. |
|
Results in Keywords For data hiding
 | DB3NF is a Rapid Web Application Development platform (RAD) designed for fast and easy creation of high performance, maintainable and scalable Web applications of virtually any kind. It also dramatically reduces development and QA time and provides a consistent look and feel throughout the application.
DB3NF consists of six main parts ordered as they appear in the development process:
DB3NF Administration console. It allows creating and maintaining application schema and business rules. It also provides application administration and deployment.
"Schema" database. Schema database structure is fixed and the data is manipulated by the Administration Console. It defines and stores application structure, business rules and basic presentation rules. This database contains a set of deployment stored procedures. They read data from the Schema database and automatically create in the target ("Data") database a third normal form table structure with all necessary tables, primary, check and foreign key constraints, indexes and stored procedures.
"Data" database. This database is created automatically and its structure depends on the application schema.
Stored procedures are created automatically by the "Schema" database procedures. No development work is required to create and modify them when application schema changes. DB3NF component "talks" to the "Data" database exclusively through these optimized stored procedures, which provides for high performance of the DB3NF platform.
DB3NF component. The component is completely generic and integrates seamlessly with both databases. No design work is required after application schema is created and deployed. DB3NF automatically "learns" application schema and rules when application starts. The component employs various caching techniques and is extremely fast and efficient.
The ASP code in DB3NF is very simple and straightforward. It is easy to write and maintain... |
|
 | Stego product for Windows with a CHAOS interface and a very large hiding capacity (~100% of carrier file)...
|
|
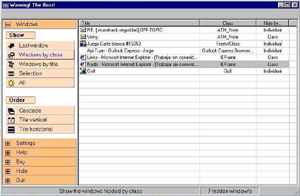 | Avoid others seeing data in your PC (message programs, bank account numbers, photographs unsuitable for children) hiding windows, applications, the icons in the systray, and mute your sound card. Try the fully version of Warning! The Boss! FOR FREE.. |
|
 | HideIt! is your personal data key.
With its help, you can easily and reliably hide any files on your home or work PC from
outsiders, and unauthorized users. Nobody except you can get access to your hidden
folders and files. No one will ever know that you made some of your files invisible to
others or even that there is some hidden data. The program itself does not require any
installation and does not create any suspicious program files or other attributes that
could attract attention and show that you are hiding your data.
But how is it possible to hide data without any complicated actions and any professional
computer skills or knowledge? The solution is as simple as HideIt!
HideIt! creates guarded and invisible space on your hard drive. This space is a private
"hiding place" where you can store private data that only you know about. The size of
this data is limited only by your hard drive capacity. The "hiding place" will be masked
by a file you can choose yourself and this file will be used as your secret data carrier
and cover. It's just impossible for anybody to find the place where your data is actually
hidden. The file you choose for hiding your data will also not be modified, its size
remains the same as it was before hiding your data. It does not matter what kind of file
you would like to use as your data hiding cover, it can be a simple text document on your
desktop or even any system file from your Windows folder. You can still use or modify
these files without any changes and it is always up to you which file you would like to
use. Such a carrier file will be used as a secret link between your hidden data and the
HideIt! program. Read more about HideIt! at http://www.guard-software.com/products/hideit/..
|
|
 | Paragon NTFS for Win98 is designed to mount NTFS partitions under Windows operating systems as normal logical drives with appropriate drive letter. Additional functionsCreating, deleting, formatting, hiding, un-hiding primary, logical or extended partitions directly under Windows (Basic FDISK functions). Paragon NTFS for Win98 includes some basic partitioning functions for creating, deleting, formatting, hiding partitions etc. These functions where taken from another our program Partition Manager. They give you the ability to create new NTFS partitions, format them, mount them under Windows 95/98/ME. The following partitioning functions are available Create partition (primary, extended and logical) Delete partition Format partition Hide / Unhide partition Set partition active / Set partition inactive (bootable / not bootable).. |
|
 | Hide Window Now allows you the privacy you have always desired at home and in your office.
It is a utility which allows you to hide the windows, and programs which are running on your desktop, without closing them. When you don't want others to see, the programs you are running, you can hide the window in seconds. Select a mouse, or keyboard method, to hide the windows. This avoids blinking minimized buttons, that show what is active on your computer. None of your (Not to read) windows will be given away, by the task bar button, while the window its self is hiding. New windows popping up can be caught and hidden.It's easy to resume work on that secret million dollar contract, when that spy sales men is gone! The program has a user-friendly interface and consumes very little system resources. It can also protect the hidden windows with a password. You can set other options too, such as muting all sounds during hiding, specifying hotkeys and so on. You can now perform the hiding action when you need to do so without delay.
Key Features:
a..
|
|
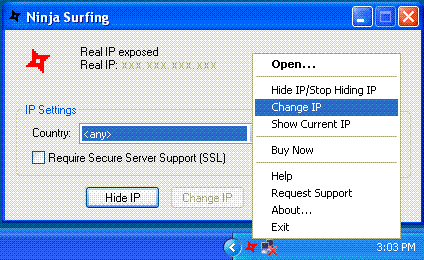 | Hide IP address with simple to use anonymity tool - Ninja Surfing. Program runs on Windows systray and provides very fast and convenient way of hiding IP address - just one click to hide IP and surf anonymously... |
|
 | Cetus StormWindow [TM] for Windows NT will allow the authorized user to add several types and degrees of protections to the desktop and system of a Windows NT computer. Intelligent use of StormWindow security measures will allow secure use of any shared Windows NT computer. Examples of desktop protections include: protecting individual desktop icons; hiding individual Start Menu program groups and links; preventing the saving of desktop changes; hiding individual drives in My Computer and Explorer; hiding the Start Menu Settings Folders (Control Panel and Printers) and/or Taskbar; and hiding the entire Network Neighborhood, or just Entire Network or Workgroup Contents within it. Some of the system protections include: disabling the MS-DOS prompt and/or the exiting to MS-DOS mode; preventing "warm booting" (Ctrl-Alt-Del) and task switching; blocking the running of Registration Editor and/or System Policy Editor; preventing the merging of .REG files into the Registry; preventing the addition or deletion of printers; keeping empty the Documents Menu; and individually hiding "sensitive" Control Panel pages and settings. StormWindow security sche.. |
|
 | Hide IP address with simple to use anonymity tool - Tiger Creep. Program runs on Windows systray and provides very fast and convenient way of hiding IP address - just one click to hide IP and surf anonymously... |
|
 | Cetus StormWindow [TM] for Windows 2000 will allow the authorized user to add several types and degrees of security to the desktop and system of any shared Windows 2000 PC... |
|
Results in Description For data hiding
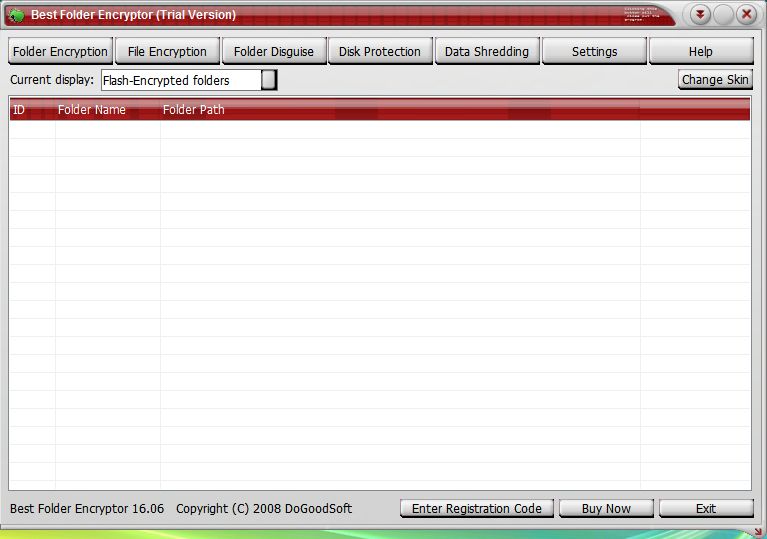 | Best Folder Encryptor quickly and safely encrypts files and folder in various ways - instant, hiding, super strong, packing and portable, and also offers enhanced features like folder disguise, disk protection, data lock, data shredding... |
|
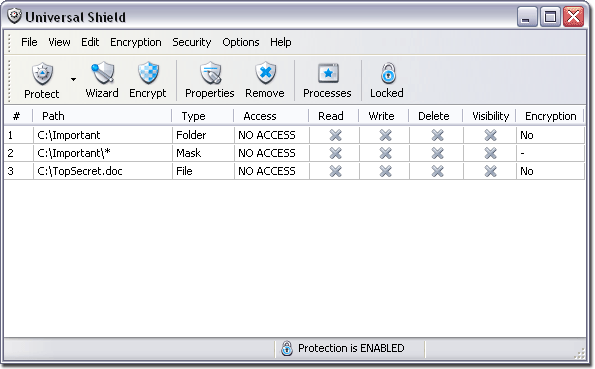 | Universal Shield 4.0 by Everstrike Software is the ultimate protection tool for your computer - hide files, folders, and drives, and set access rules using flexible security combinations for your most precious data. A unique feature of Universal Shield is the perfect combination of data hiding and encrypting. This feature is very important nowadays when everybody knows that information is money, and information security and protection is very important. The program has been especially designed to be the most flexible security tool on the market, suitable both for home use and in corporate environments. Universal Shield features include hiding files, folders, and drives on a local computer from local users, including administrators; setting access rights for particular files and disks; and preventing the deletion of specific files. Password-protect your data, program start-up, or program uninstall. Secure your data not only from local users, but network and Internet users as well. Use hotkeys to show and hide folders without actually running the program. Or, run the program in Stealth mode so that other users do not know about it. Set trusted processes, which will not be under protection; for example, some program will work with the hidden data, but users are unable to access that data. The new Universal Shield 4.0 version includes a variety of new features. Data encryption is processed with the help of nine algorithms. A variety of security tricks is available as well - you can prohibit access to folders like My Documents, Favorites, and History, as well as restrict access to the Control Panel, or prevent desktop and date/time adjustment. The new version also contains a wizard, which includes an option of restricting personal folders and settings, as well as files/folders/drives protection, a hiding expert, and a data encryption master. Universal Shield runs on Microsoft Windows NT/2000/XP/2003 Server...
|
|
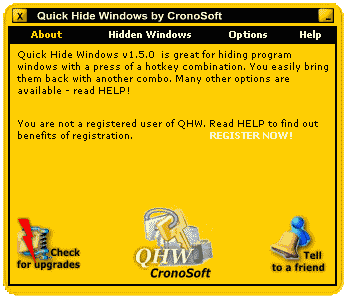 | Quick Hide Windows by CronoSoft is great for hiding program windows with a press of a hotkey combination. You easily bring them back with another combo. Hiding the taskbar and desktop icons is just awesome. Password protection allows you to lock QHW to prevent intruders from trying to show invisible applications while you're gone. You can even lock your computer with QHW instead of a weak, easily hackable screensaver password... |
|
 | Cetus StormWindow [TM] for Windows NT will allow the authorized user to add several types and degrees of protections to the desktop and system of a Windows NT computer. Intelligent use of StormWindow security measures will allow secure use of any shared Windows NT computer. Examples of desktop protections include: protecting individual desktop icons; hiding individual Start Menu program groups and links; preventing the saving of desktop changes; hiding individual drives in My Computer and Explorer; hiding the Start Menu Settings Folders (Control Panel and Printers) and/or Taskbar; and hiding the entire Network Neighborhood, or just Entire Network or Workgroup Contents within it. Some of the system protections include: disabling the MS-DOS prompt and/or the exiting to MS-DOS mode; preventing "warm booting" (Ctrl-Alt-Del) and task switching; blocking the running of Registration Editor and/or System Policy Editor; preventing the merging of .REG files into the Registry; preventing the addition or deletion of printers; keeping empty the Documents Menu; and individually hiding "sensitive" Control Panel pages and settings. StormWindow security sche..
|
|
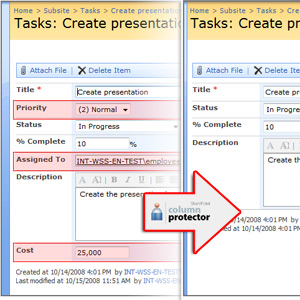 | Hiding columns on SharePoint lists. Blocking data in columns for selected users. Selectively securing data from specified users without the necessity of blocking their permissions to the whole element on a SharePoint list... |
|
 | Hide Window Now allows you the privacy you have always desired at home and in your office.
It is a utility which allows you to hide the windows, and programs which are running on your desktop, without closing them. When you don't want others to see, the programs you are running, you can hide the window in seconds. Select a mouse, or keyboard method, to hide the windows. This avoids blinking minimized buttons, that show what is active on your computer. None of your (Not to read) windows will be given away, by the task bar button, while the window its self is hiding. New windows popping up can be caught and hidden.It's easy to resume work on that secret million dollar contract, when that spy sales men is gone! The program has a user-friendly interface and consumes very little system resources. It can also protect the hidden windows with a password. You can set other options too, such as muting all sounds during hiding, specifying hotkeys and so on. You can now perform the hiding action when you need to do so without delay.
Key Features:
a..
|
|
 | Avoid others seeing data in your PC (message programs, bank account numbers, photographs unsuitable for children) hiding windows, applications, the icons in the systray, and mute your sound card. Try the fully version of Warning! The Boss! FOR FREE.. |
|
 | FantoMASK based on Russian Standard of Cryptography and algorithm of MASKing and hiding data developed specially for military use, allows transmitting and storing confidential information remaining above suspicion. Key file, encrypted and masked by FantoMASK is included in this package. .. |
|
 | This is a nice version of the memory puzzle game where you have to match similar flowers in the garden. But hurry up as you have to do this before the sun sets or you will lose. Also watch out for Goofy Gopher because if you pick a plant, Goofy is hiding under then he'll rearrange your garden. So you will have to remember the location of the flowers all over again.
Left Click on a plant to view the flower and then Left Click on any other plant where you think a similar flower is hiding, to match them... |
|
 | Paragon NTFS for Win98 is designed to mount NTFS partitions under Windows operating systems as normal logical drives with appropriate drive letter. Additional functionsCreating, deleting, formatting, hiding, un-hiding primary, logical or extended partitions directly under Windows (Basic FDISK functions). Paragon NTFS for Win98 includes some basic partitioning functions for creating, deleting, formatting, hiding partitions etc. These functions where taken from another our program Partition Manager. They give you the ability to create new NTFS partitions, format them, mount them under Windows 95/98/ME. The following partitioning functions are available Create partition (primary, extended and logical) Delete partition Format partition Hide / Unhide partition Set partition active / Set partition inactive (bootable / not bootable).. |
|
Results in Tags For data hiding
 | Apimac Secret Folder lets you conceal a folder and its contents. It provides you with an easy and fast way to protect documents and avoid them being seen, modified, or erased by other users (either on a network or uninvited!)... |
|
 | HideIt! is your personal data key.
With its help, you can easily and reliably hide any files on your home or work PC from
outsiders, and unauthorized users. Nobody except you can get access to your hidden
folders and files. No one will ever know that you made some of your files invisible to
others or even that there is some hidden data. The program itself does not require any
installation and does not create any suspicious program files or other attributes that
could attract attention and show that you are hiding your data.
But how is it possible to hide data without any complicated actions and any professional
computer skills or knowledge? The solution is as simple as HideIt!
HideIt! creates guarded and invisible space on your hard drive. This space is a private
"hiding place" where you can store private data that only you know about. The size of
this data is limited only by your hard drive capacity. The "hiding place" will be masked
by a file you can choose yourself and this file will be used as your secret data carrier
and cover. It's just impossible for anybody to find the place where your data is actually
hidden. The file you choose for hiding your data will also not be modified, its size
remains the same as it was before hiding your data. It does not matter what kind of file
you would like to use as your data hiding cover, it can be a simple text document on your
desktop or even any system file from your Windows folder. You can still use or modify
these files without any changes and it is always up to you which file you would like to
use. Such a carrier file will be used as a secret link between your hidden data and the
HideIt! program. Read more about HideIt! at http://www.guard-software.com/products/hideit/..
|
|
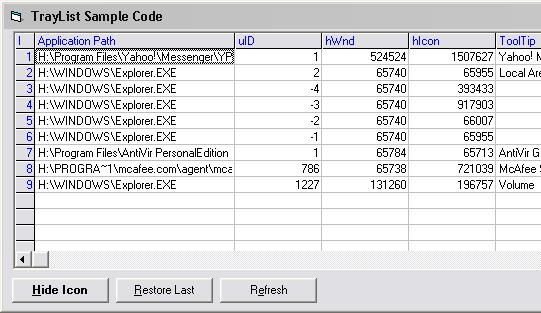 | Easily get all system tray icons form your applications. Use STI to get all of the information of the applications running in systray area... |
|
 | Paragon NTFS for Win98 is designed to mount NTFS partitions under Windows operating systems as normal logical drives with appropriate drive letter. Additional functionsCreating, deleting, formatting, hiding, un-hiding primary, logical or extended partitions directly under Windows (Basic FDISK functions). Paragon NTFS for Win98 includes some basic partitioning functions for creating, deleting, formatting, hiding partitions etc. These functions where taken from another our program Partition Manager. They give you the ability to create new NTFS partitions, format them, mount them under Windows 95/98/ME. The following partitioning functions are available Create partition (primary, extended and logical) Delete partition Format partition Hide / Unhide partition Set partition active / Set partition inactive (bootable / not bootable)..
|
|
 | "How do I keep my surfing on the net secret from people around me ? How do I prevent prying eyes from sensitive information.when I surf on the net ? How do I avoid popup advertises when I surf the net ? This is not a fancy web browser, what it does is for your privacy from people around you, at home or office. If you don't like people nosy about what you're browsing on the net, or when you're surfing at the sites that you do not want people around you to know. You just press a combination of keys (called Secret keys or Hot keys) then this web browser disappeared on screen, not even on the taskbar. When they go away, all you have to do is again to press a different set of combination of keys and this browser will come back to life again.".. |
|
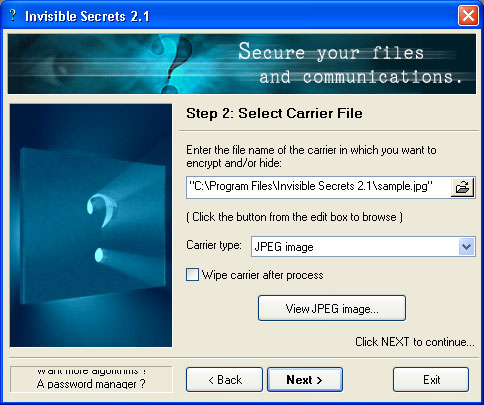 | Steganography: an excellent method of embedding information on the contents of the file within another file! Make your secrets invisible in just 3 quick steps!..
|
|
 | Free program for hiding information in video. After info hiding you can compress video with unknown codec (this is main feature) and extract you file from this video later! Program advices lrelatively low noise level... |
|
 | Cetus StormWindow [TM] for Windows NT will allow the authorized user to add several types and degrees of protections to the desktop and system of a Windows NT computer. Intelligent use of StormWindow security measures will allow secure use of any shared Windows NT computer. Examples of desktop protections include: protecting individual desktop icons; hiding individual Start Menu program groups and links; preventing the saving of desktop changes; hiding individual drives in My Computer and Explorer; hiding the Start Menu Settings Folders (Control Panel and Printers) and/or Taskbar; and hiding the entire Network Neighborhood, or just Entire Network or Workgroup Contents within it. Some of the system protections include: disabling the MS-DOS prompt and/or the exiting to MS-DOS mode; preventing "warm booting" (Ctrl-Alt-Del) and task switching; blocking the running of Registration Editor and/or System Policy Editor; preventing the merging of .REG files into the Registry; preventing the addition or deletion of printers; keeping empty the Documents Menu; and individually hiding "sensitive" Control Panel pages and settings. StormWindow security sche.. |
|
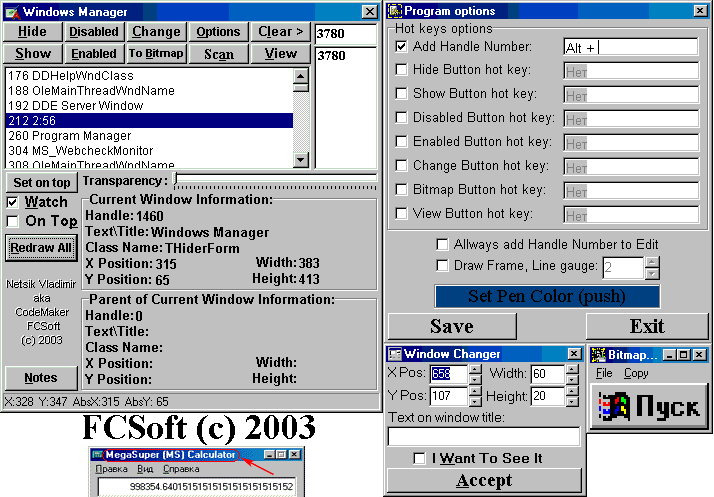 | Program to read/set position & text; change transparency,hiding&active state, view all coordinates, class name selected & parent window via Handle. New version: Allows to change "stay on top" status by handle... |
|
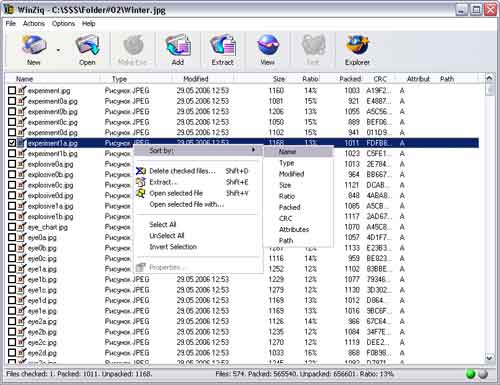 | Insider creates compressed archives and works with these files while the archives themselves are not evident on the user.. |
|
Related search : ile youhiding yourhideit hideit,hiding your data,ntfs forparagon ntfs,deleting formatting hidingsoftware paragon ntfswin98 software paragonpeople around,,preventing the,,Order by Related
- New Release
- Rate
hiding dictionary -
file hiding -
information hiding -
hiding file -
hiding a file -
|
|























