Order by
Related
-
New Release
-
Rate
Results in Description For
breach
 | Any falsification of information was labeled cheating. Answer sheets that failed the test for independent marking received a score of zero. Students wanting to protest to the Student Disciplinary Committee were offered assistance. Not one student protested. Cheating complaints by classmates dropped to near zero. Students named the software The Cheat Checker.
The Cheat Checker examines similar pairs of answer sheets for independent marking. Any pair that fails the test is labeled presumptive cheating. The Cheat Checker then examines the uniqueness of this pair with respect to the entire class. A significant finding for uniqueness and for presumptive cheating is labeled confirmed. Cheating has always been a problem with multiple choice tests. The Cheat Checker helped honest students relax knowing they did not have to compete with those who did cheat.
The original Cheat Checker examined one version of a test at a time. There was little need for multiple version tests when using the Cheat Checker in classes of 120 students. There was one exception: When a student was reported to the Student Disciplinary Committee for cheating, only one member fully understood the significance of the results. The committee quickly discovered that the lower the grade, the easier to detect cheating. This was considered unfair. Faculty are more familiar with and accepting of multiple version test results.
Students have learned to breach the expected security given by multiple version tests. The current Cheat Checker examines all versions of a test as marked.
The structure for each answer file is: nine character ID:one space:answer string. The answer key ID is 999000111. Student records follow the answer key.
A Rule of Thumb for Cheating is five to seven consecutive identical pairs of wrong answers distributed in a string of paired right answers... |
|
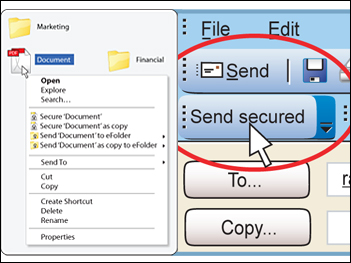 | ePrivacy Suite - The Ultimate Content Encryption Solution
Protecting intellectual property and customer data are top security concerns for any business today. Whether in transit over a network or at rest on a system, encryption helps secure information, minimizing the risk of being altered or accessed by unauthorized internal and external users. The ePrivacy Suite allows companies to address security and regulatory requirements by encrypting files and email with a centrally managed solution, therefore eliminating security breach risks such as financial loss, brand damage and lawsuits.
Data in transit:
The ePrivacy Suite combines our award-winning email encryption with file and folder encryption allowing a company of any size to secure data in transit and data at rest. Email has become one the most used forms of communication for both private and business users. For organizations, it is a critical medium for communicating, collaborating and sharing information within and between organizations. It is also the number one source of security risk. Any corporate mail server or workstation currently sending and receiving email messages is vulnerable to attacks. Secured eMail protects sensitive information from point A to point B and does not change the behavior of email users, as they simply press the Send Secured button, and their sensitive information will be sent through an encrypted channel.
Data at Rest:
Business critical information is stored in multiple locations within the enterprise - on PCs, laptops, server and storage devices. Enterprises need privacy management solutions that ensure sensitive information is protected from unauthorized access as well as eliminate the risks associated with losing mobile storage devices. Secured eF2 can secure both local and networked files/folders...
|
|
Results in Tags For
breach
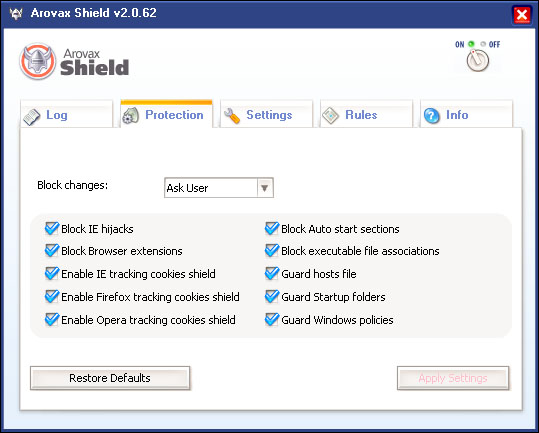 | Arovax Shield software is dedicated to protect the home user's privacy. It Detects and Notifies you about all the Major online threats tried to penetrate your System, Isolates & Removes them. Arovax Shield protects your PC with bulletproof security from both known and unknown threats before they even get on your Personal Computer. Not a tech wiz? No problem - an easy-to-use interface and pre-loaded settings take the guesswork out of security. Don't hesitate. Download Arovax Shield now. Its completely free... |
|
breach of contract cases -
security breach database -
2010 security breach -
ecmc security breach -
2012 security breach -


